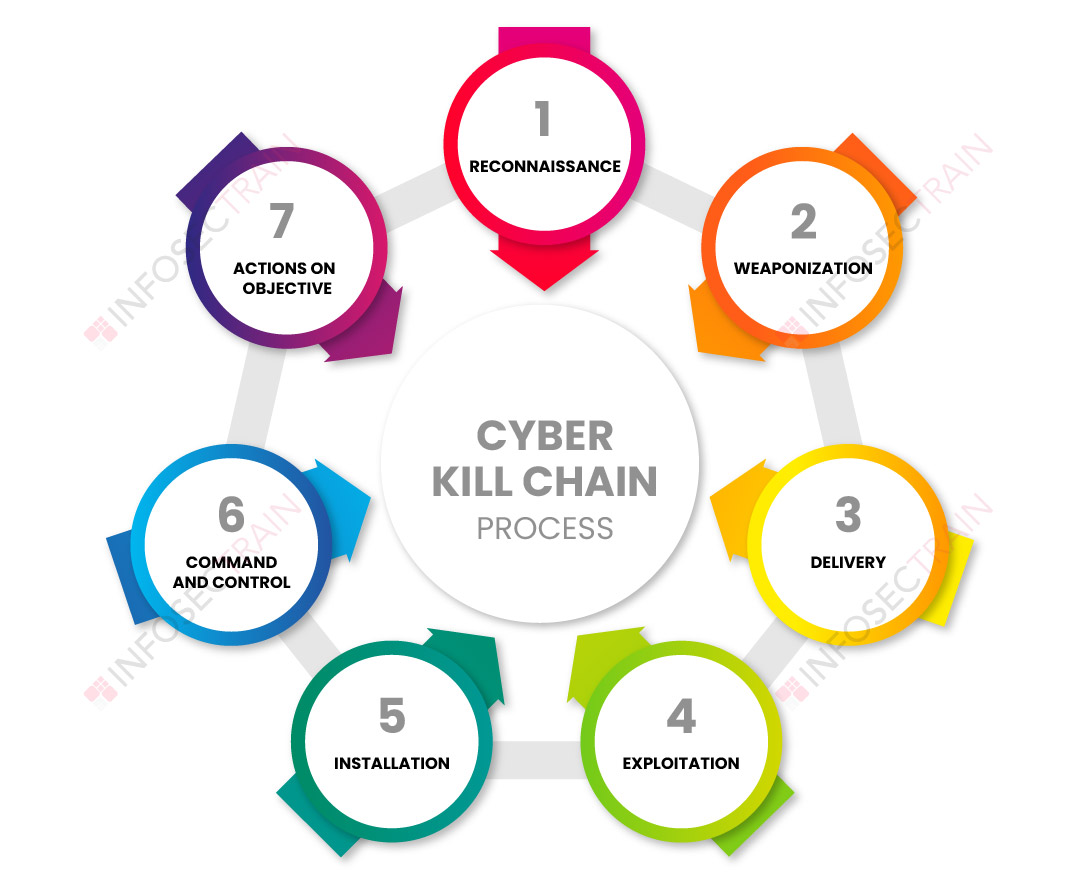
![Lockheed Martin Cyber Kill Chain (CKC) [22] seven steps. The part that... | Download Scientific Diagram Lockheed Martin Cyber Kill Chain (CKC) [22] seven steps. The part that... | Download Scientific Diagram](https://www.researchgate.net/publication/335024682/figure/fig1/AS:789313017098241@1565198296990/Lockheed-Martin-Cyber-Kill-Chain-CKC-22-seven-steps-The-part-that-is-specified-with.png)
Lockheed Martin Cyber Kill Chain (CKC) [22] seven steps. The part that... | Download Scientific Diagram

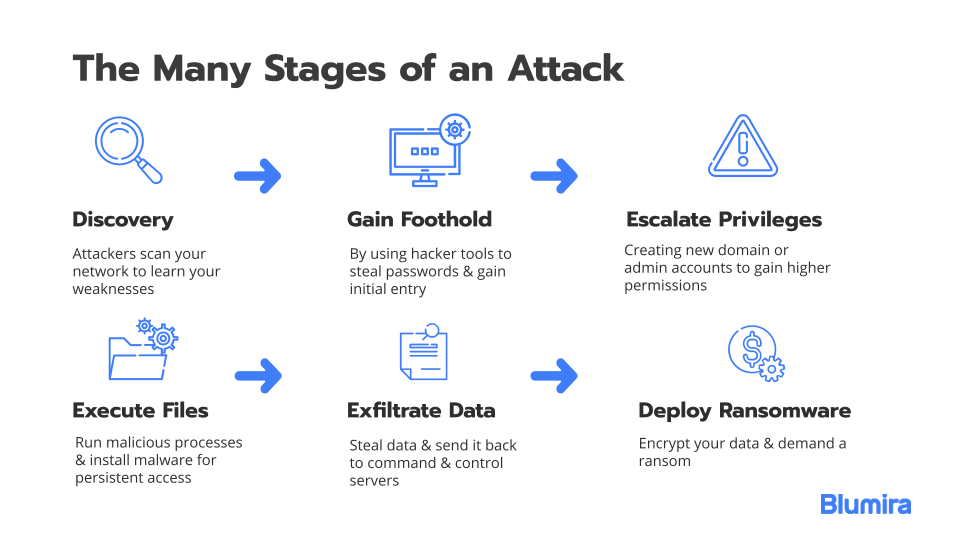
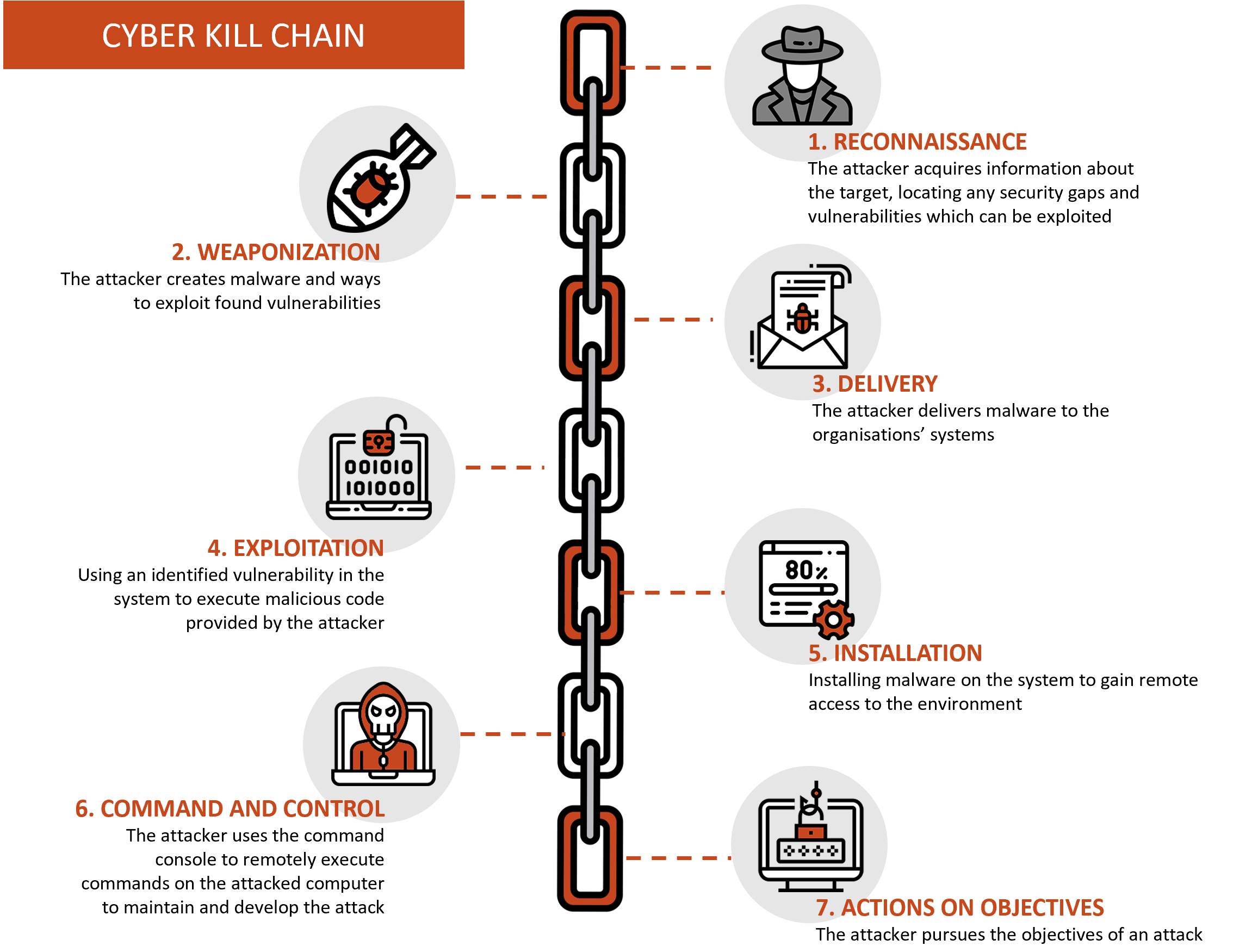
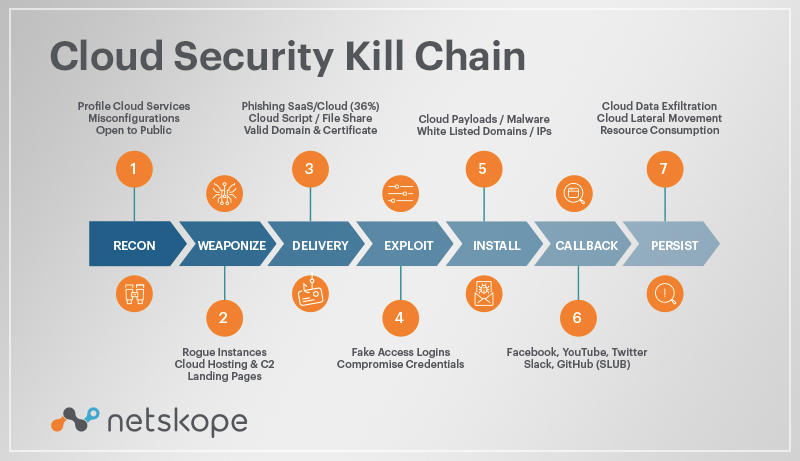
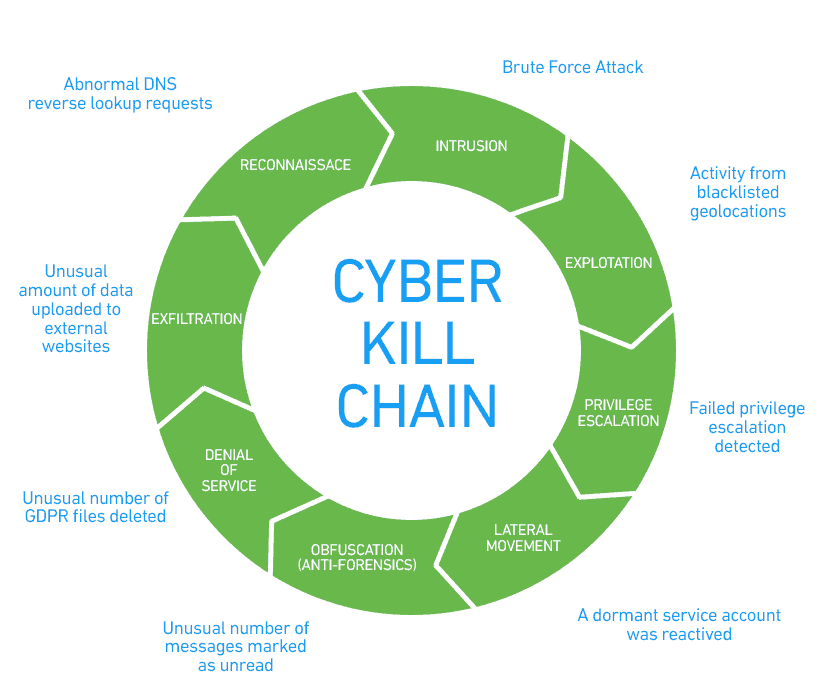
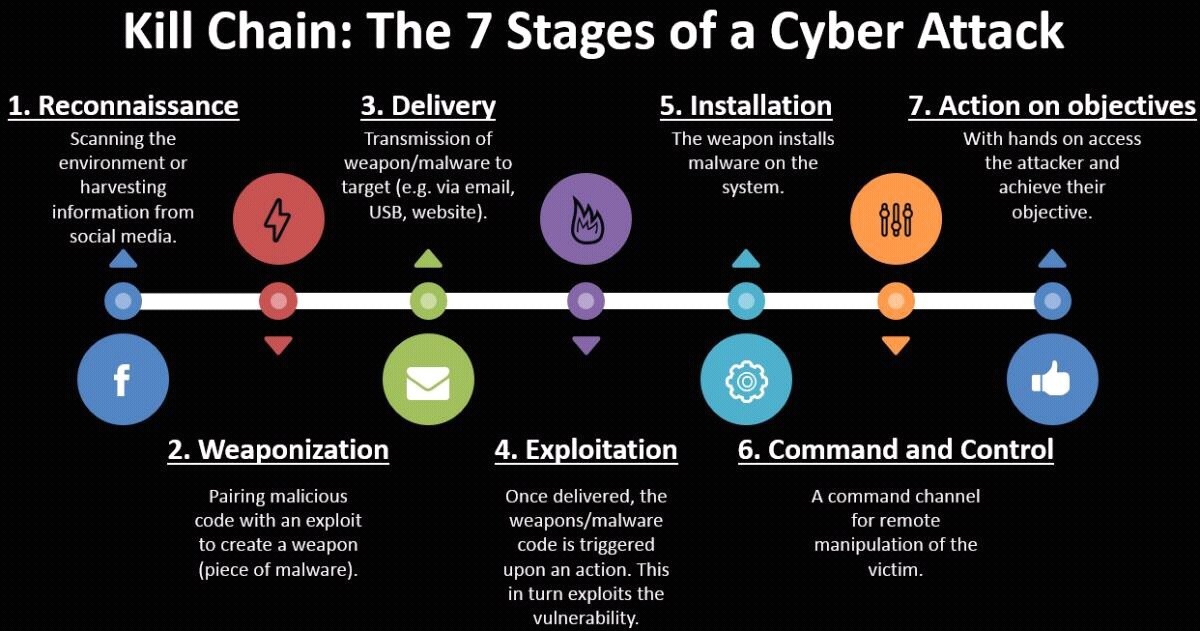
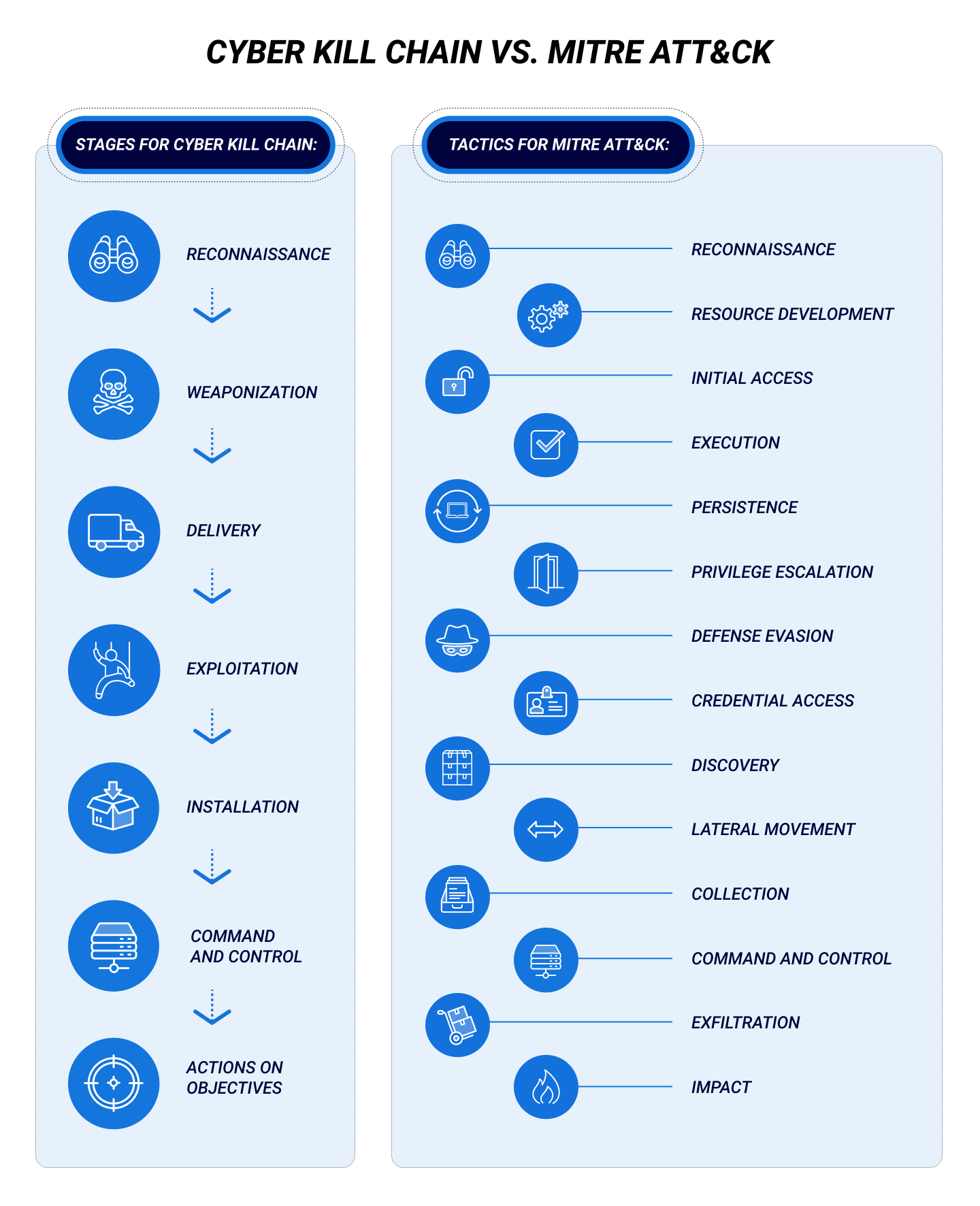
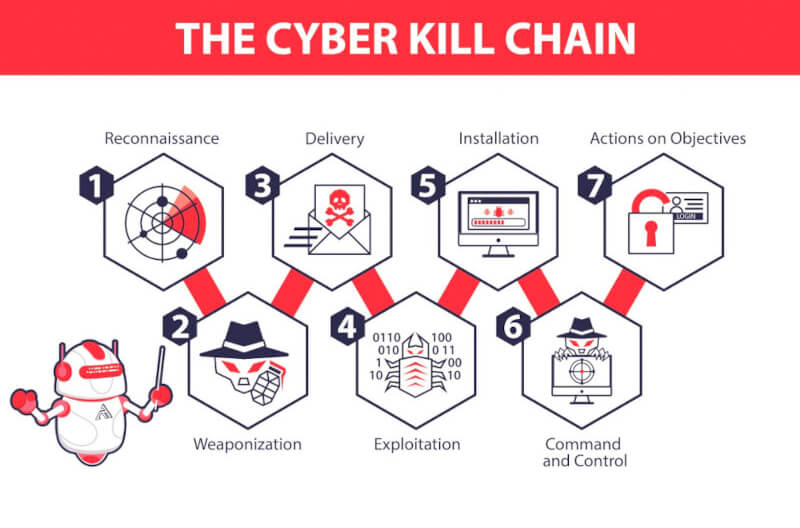
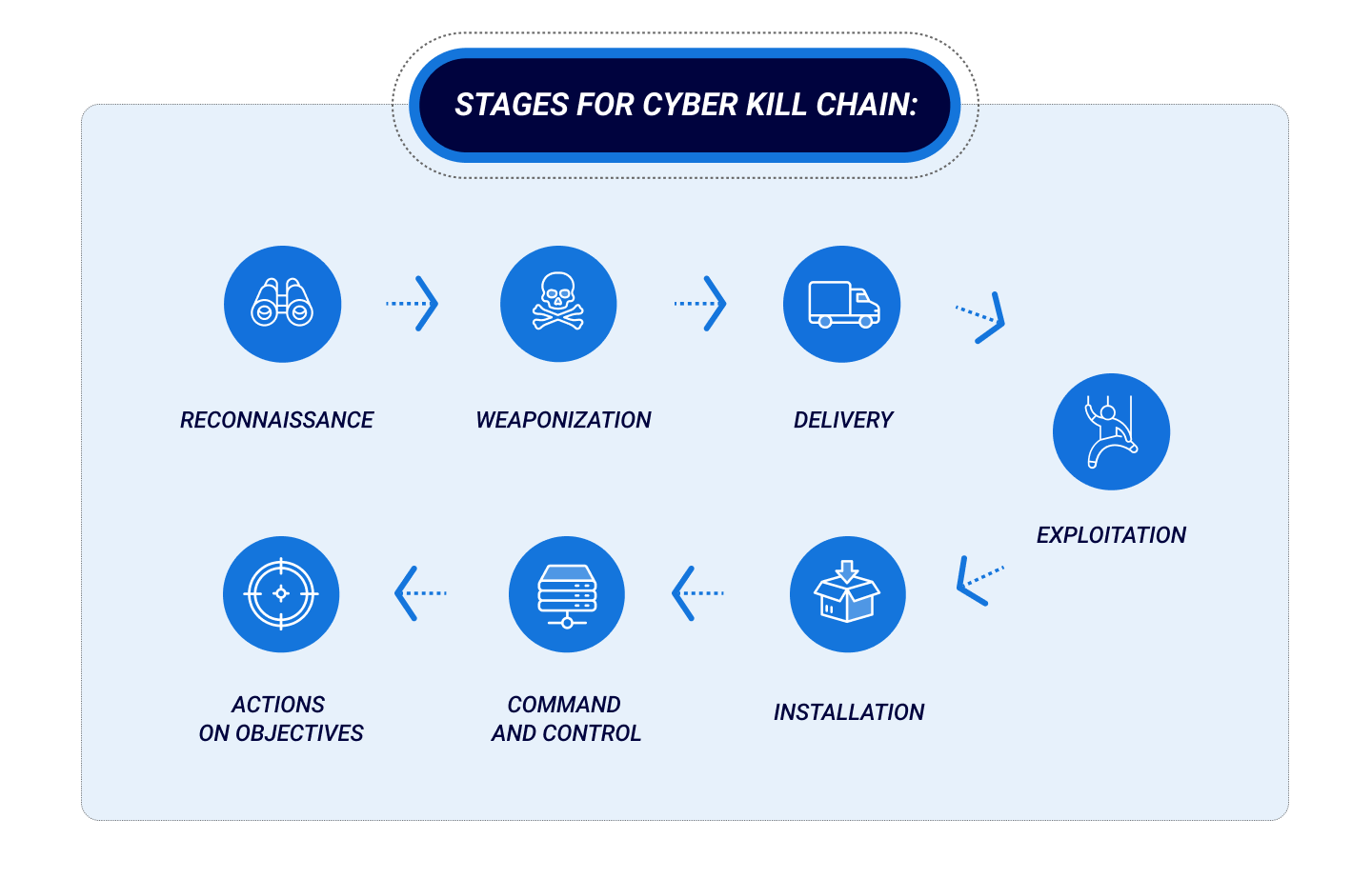
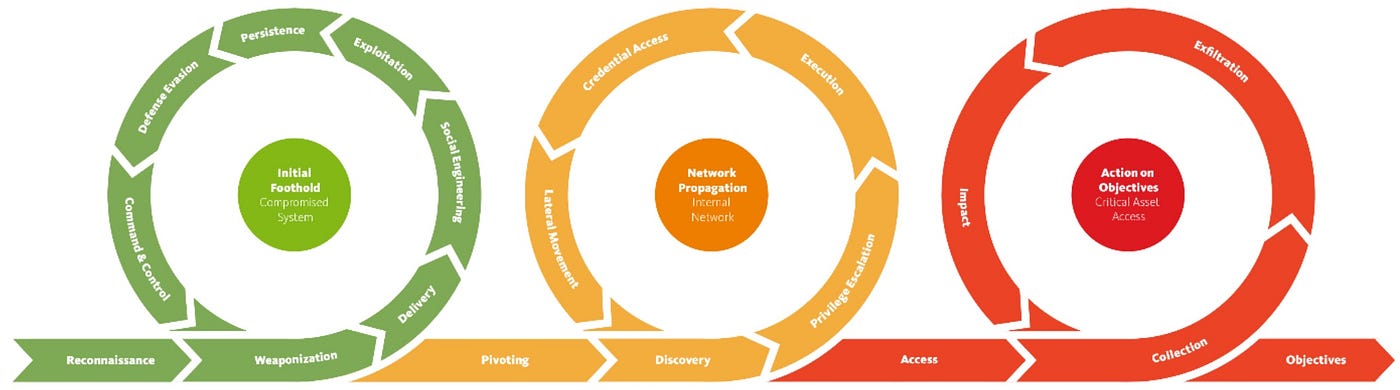
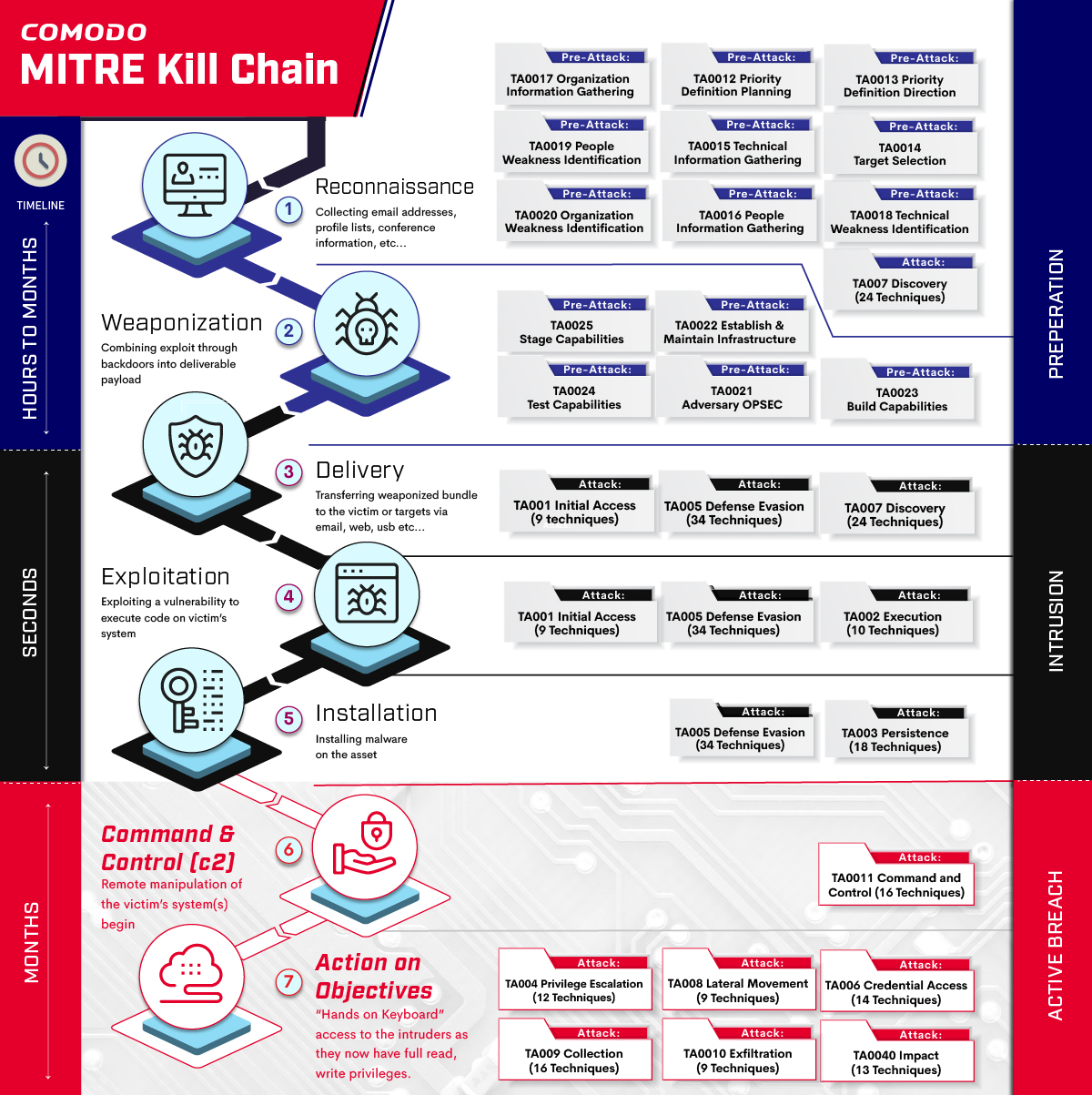
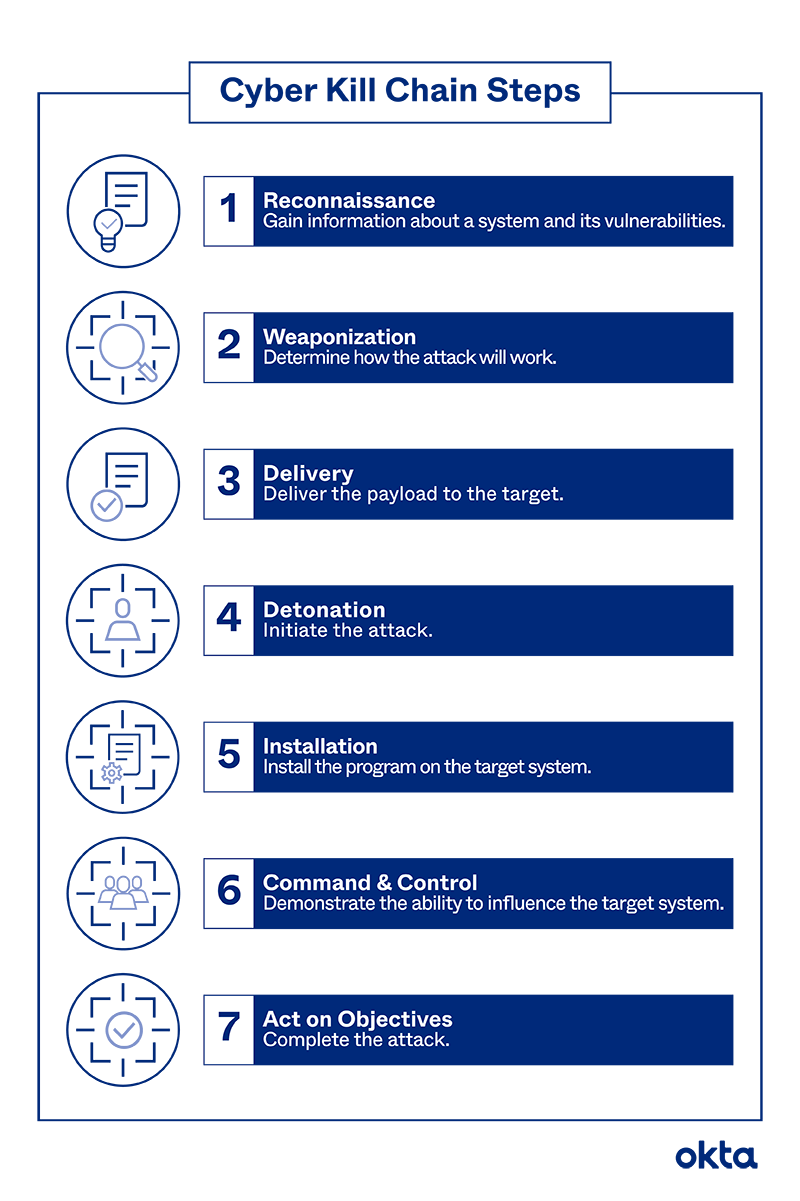
EC-Council - The cyber kill chain helps prepare the organization for all common threats such as network breaches, data thefts, ransomware attacks, and advanced persistent attacks. Let's read more about the cyber